
In an era where digital threats are evolving rapidly, artificial intelligence (AI) has emerged as a critical component in fortifying cybersecurity measures. The increasing sophistication of cyber-attacks requires equally advanced defence mechanisms, and AI's capabilities in pattern recognition, predictive analysis, and real-time response are proving invaluable. This article looks into some of the applications, benefits, and challenges of AI in cybersecurity, providing a comprehensive overview for both general audiences and tech enthusiasts.
Artificial intelligence in cybersecurity leverages machine learning algorithms, natural language processing, and data analytics to identify and respond to threats. AI development services in this domain focus on analyzing vast amounts of data from network traffic, user behavior, and threat intelligence reports. By recognizing patterns and anomalies, these systems can detect potential security breaches more efficiently than traditional methods. One of the key strengths of AI is its ability to learn and adapt continuously, enhancing the accuracy and effectiveness of cybersecurity measures.
Machine learning models are trained on historical data, enabling them to identify known threats and predict new ones. This continuous learning process enhances the accuracy and effectiveness of cybersecurity measures, allowing for proactive defense strategies rather than reactive responses.
AI-powered cybersecurity systems excel in threat detection and prevention. Traditional security measures often rely on rule-based systems that can only identify known threats. In contrast, AI can detect zero-day vulnerabilities and advanced persistent threats (APTs) by analyzing behavior patterns and anomalies.
Data protection and privacy are paramount concerns. AI can bolster these areas by implementing advanced encryption techniques and monitoring access controls.
AI can help enforce compliance with regulations such as GDPR and CCPA. It can automate compliance checks, monitor data access, and generate alerts for violations. Furthermore, AI enhances identity and access management (IAM) systems by analyzing user behavior patterns to detect anomalies that may indicate compromised credentials or unauthorized access attempts.
One of the most significant advantages of AI in cybersecurity is its ability to automate incident response and recovery processes. In the event of a cyber attack, a timely and efficient response is crucial.
A notable example of AI's application is its use in the financial sector. JPMorgan Chase implemented an AI-based system known as Contract Intelligence (COiN) to analyze legal documents and extract critical data points. This system has significantly improved the efficiency and accuracy of document analysis and enhanced the bank's ability to detect potential compliance issues and fraudulent activities.
This application is closely related to the specialized need for ai in credit risk management, where vast amounts of transaction and behavioral data must be analyzed for anomaly detection and forecasting risk. Statistics have shown that JPMorgan Chase & Co. reduced their default rates by 20% and operational costs by 15% within the first year.
While the benefits are substantial, challenges and ethical considerations must be addressed. Bias in AI algorithms is a primary concern; if training data is biased, the resulting systems may exhibit discriminatory behavior. Continuous monitoring and evaluation of AI systems are necessary to identify and address any biases. Furthermore, data privacy is critical, requiring robust measures to protect sensitive information and ensure compliance with data protection regulations.
The future of AI in cybersecurity is promising, with ongoing advancements poised to enhance its capabilities further. AI is being integrated with other emerging technologies, such as blockchain and the Internet of Things (IoT), to create comprehensive cybersecurity solutions. Organizations must stay abreast of these advancements and continuously adapt their strategies to leverage the latest AI capabilities.
Artificial intelligence is revolutionizing cybersecurity by enhancing threat detection, data protection, and incident response processes. The real-world applications demonstrate the tangible benefits of Custom AI solutions in safeguarding digital assets and ensuring the integrity of critical systems. If you're ready to fortify your digital defenses with advanced AI development services that offer unparalleled protection, contact us for a cybersecurity AI consultation and secure your digital future today.
Unlock PropTech automation. Learn how our custom AI uses Computer Vision and geometric reasoning to extract data from floor plans, reducing costs.
.png)
Automate grading, curriculum mapping, and student records. See 5 top use cases where IDP and OCR transform academic operations.

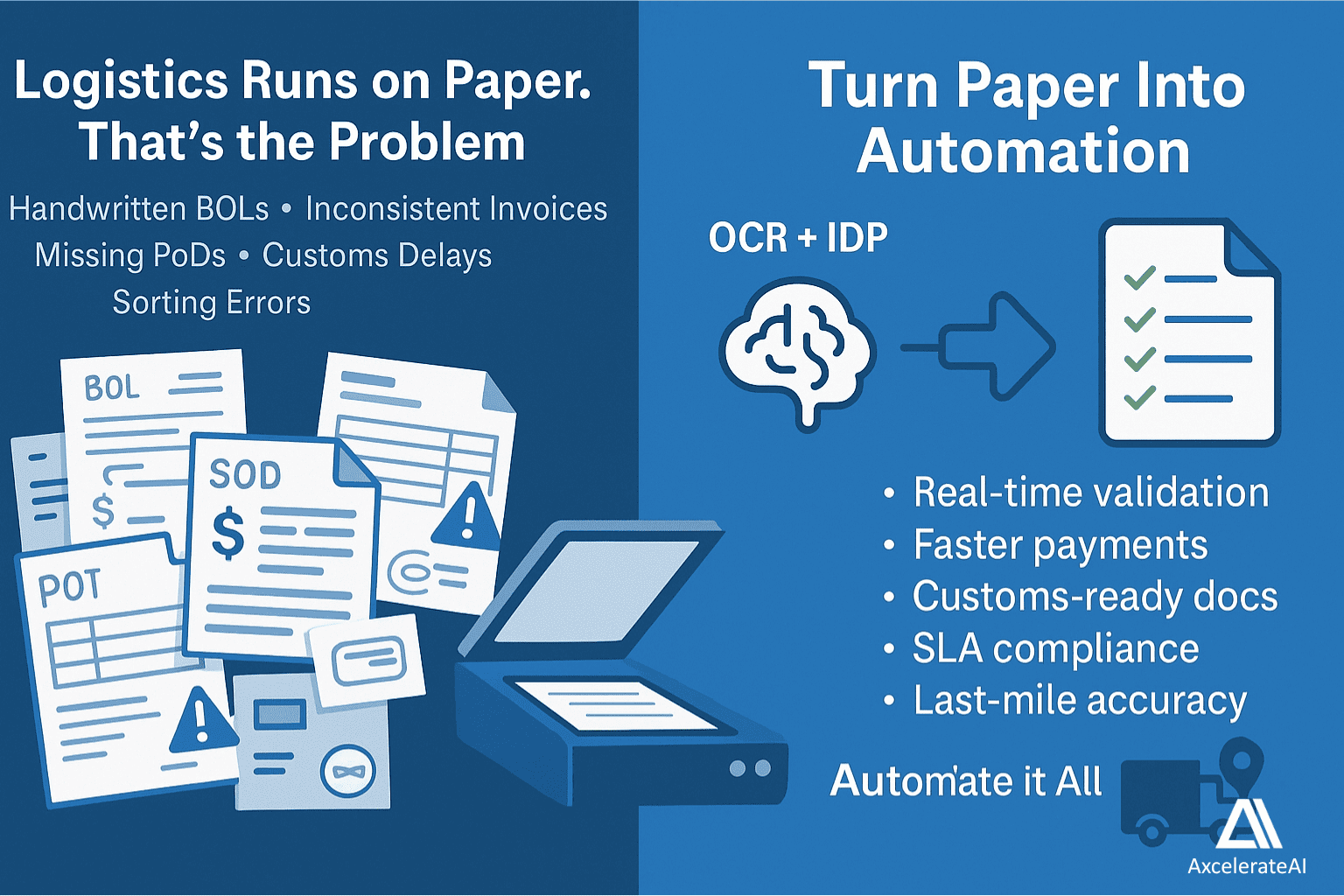
Unlock logistics efficiency with OCR and IDP: Automate inventory, supply chain tracking, and compliance. See real examples from DHL and Maersk.


Unlock PropTech automation. Learn how our custom AI uses Computer Vision and geometric reasoning to extract data from floor plans, reducing costs.

.png)
Automate grading, curriculum mapping, and student records. See 5 top use cases where IDP and OCR transform academic operations.


Unlock logistics efficiency with OCR and IDP: Automate inventory, supply chain tracking, and compliance. See real examples from DHL and Maersk.
